CVE Explained CVE-2023-34362
Having a deep dive into the moveit vulnerability
Product affected
Progress MOVEit versions before :
2021.0.6 (13.0.6)
2021.1.4 (13.1.4)
2022.0.4 (14.0.4)
2022.1.5 (14.1.5)
2023.0.1 (15.0.1)
MOVEit Transfer is a file transfer application allowing users to transfer files between different systems securely. It is used by businesses of all sizes to transfer files between offices, customers, and partners.
Vulnerablity
A SQL injection vulnerability has been found in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain access to MOVEit Transfer's database.
Impact , Persistance and how to detect
After successfully exploiting the vulnerability, the attacker deploys a web shell (human.aspx), a hidden entry point for future access. Through this deployed web shell, the threat actor gains continued backdoor access to the compromised system, establishing a means for continuous control. Subsequently, they initiate data exfiltration activities, secretly extracting sensitive information without authorization.
It is important to note that certain patterns of requests are frequently observed when attempting to implant malicious web shells. These patterns of requests on server often serve as indicators of compromise and include:
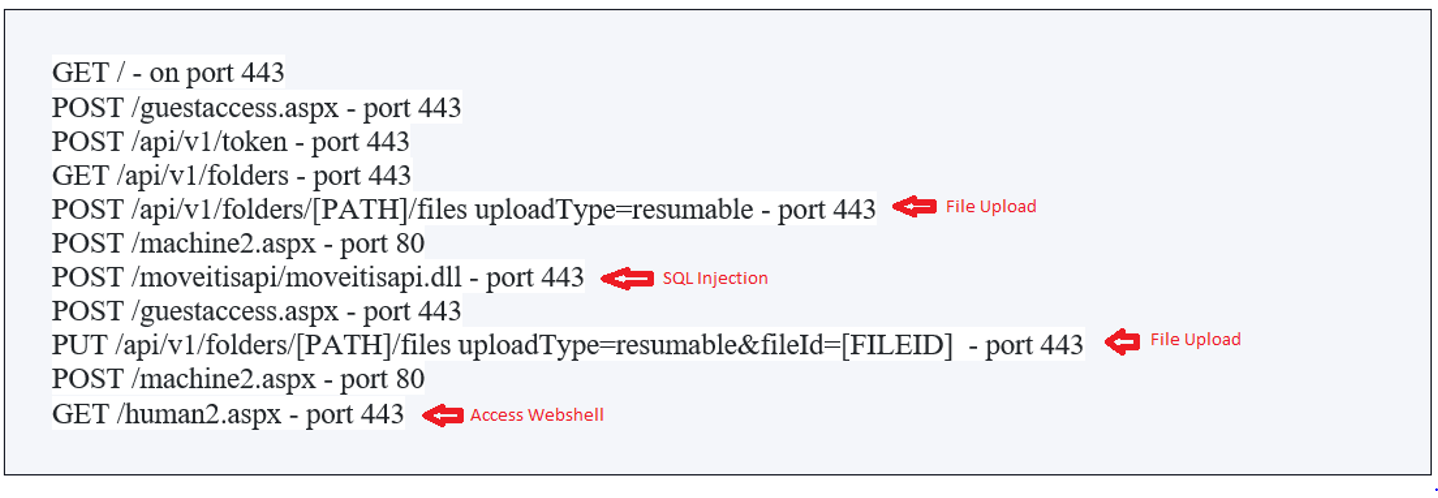
/api/v1/token: an endpoint used for checking a session token.
/api/v1/folders: an endpoint used for “folder actions and its properties”.
dll: is used to perform SQL injection when requested with specific headers.
aspx: is used to prepare a session and extract CSRF tokens.
Flow of exploit
The exploit as 1. Exploit the SQL injection and obtain the sysadmin API access token 2. Use this token to abuse a deserialization vulnerability 3. Thus allowing Remote code execution
The bug was in the MOVEitISAPI.dll which while processing the headers in a HTTP request Code to make the HTTP request to guestaccess.aspx
Function Purpose: The
set_session_variablesfunction is designed to manipulate session variables of the MOVEit Transfer's session, exploiting a vulnerability inMOVEitISAPI.dll.Header Manipulation Technique:
The
MOVEitISAPI.dllis tricked into forwarding the request to a specific internal component (SILMachine2) by using a custom headerxx-silock-transactionwith the valuefolder_add_by_path.Normally,
MOVEitISAPI.dlllooks forX-siLock-Transactionto determine the transaction type. However, due to a bug, it can be deceived by a similar header (xx-silock-transaction).By using two headers, one with a prefix (
xx-silock-transaction) and the actual one (X-siLock-Transaction), the function is able to manipulate the transaction type and pass specific session variables.
Exploiting the Bug:
The
xx-silock-transaction: folder_add_by_pathheader matches a condition inMOVEitISAPI.dll, causing the request to be passed tomachine2.aspx.The
X-siLock-Transaction: session_setvarsheader, which is only processed bymachine2.aspx, forwards the request toguestaccess.aspx.The
session_setvarsin theX-siLock-Transactionheader contains the session variables needed to manipulate the session and forward the request successfully toguestaccess.aspx.
The pic shows the session variables in the guestaccess.aspx file
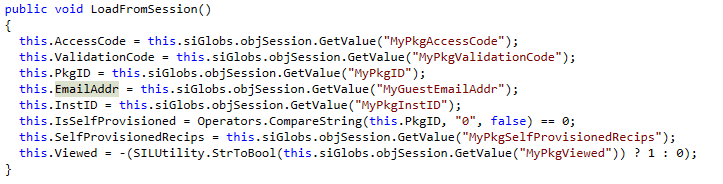
Session variables (Source)
The POST request is sent to guestaccess.aspx with headers such as “MyUsername”, “MyPkgAccessCode” and “MyGuestEmailAddr” set so as to generate a CSRF token needed to create the session.
Function Purpose: This Python function is designed to retrieve a Cross-Site Request Forgery (CSRF) token from the MOVEit Transfer software. The CSRF token is required to perform further actions, specifically triggering a SQL injection in the guestaccess.aspx page.
CSRF Token Retrieval:
The function sends a POST request to
guestaccess.aspxwith specific data to trigger the generation of a CSRF token for the current session.The
datadictionary contains required parameters, and one key-value pair,"Arg06": "123", is crucial for generating a page with a CSRF token.The request is made using the
requestslibrary, and the response is stored in the variabler.
CSRF Token Extraction:
The HTML body of the response is obtained and stored in the variable
body.The function uses a regular expression (
re.search) to find the CSRF token from the HTML response.If a match is found, the CSRF token is extracted and returned. If not,
Noneis returned.
SQL Injection Triggering:
The CSRF token obtained can be subsequently used to trigger a SQL injection in the
guestaccess.aspxpage by including it in requests.
Code to trigger SQL injection
The session_vars headers that contain the injection vulnerability are treated by the MOVEit application as a list of email addresses. The MOVEit application then splits the list with commas as delimiter before passing it to the SQL engine.
Checking for Commas:
The function iterates through the list of SQL statements provided as
sql_statements.It checks each statement for the presence of a comma. If a comma is found, an exception is raised, as the vulnerability does not work with commas. This is because the target field in the MOVEit application splits input on commas, treating them as separators in a list of email addresses.
Injecting SQL Statements:
The function then iterates through the SQL statements again.
For each SQL statement, it prepares a dictionary named
session_varswith key-value pairs that are to be injected into the session.The key
MyPkgIDis set to"0". This might be a required field for the operation.The key
MyPkgSelfProvisionedRecipsis where the actual SQL injection takes place. The value is crafted in a way to terminate any existing query (SQL Injection');) and then insert the attacker's SQL command ({sql_statement} -- asdf).
Executing the Injection:
set_session_variablesfunction is called with the craftedsession_vars, which sets these variables in the current session, effectively preparing the SQL injection.do_guest_accessfunction is then called, which likely uses the manipulated session variables and triggers the actual SQL injection by accessing a specific part of the MOVEit application (possiblyguestaccess.aspx).
We can then create a JSON Web Token and using which we can obtain the sysadmin API access token.
With the sysadmin access, we can manipulate the database by retrieving/uploading/updating data and delete files.
Now since we have the folder if the code we can delete the files in the db:
Code to delete files in the database. In this PoC, the script writes a file to C:\Windows\Temp\message.txt. Using various methods we can upload alternative payloads to the target machine. This code uploads the file in the database:
The p dictionary contains parameters for the HTTP request. In this case, it specifies that the upload type is "resumable." The d dictionary contains data related to the file being uploaded. It includes the file name ("letusin"), size ("0"), and comments, which is set to the payload.
FINALYY !!! Now to achieve remote code execution we need the State value in the database to contain the encoded serialized payload. As we can see above , the payload is in the ‘comments’ field. By using SQL injection we can copy the value of ‘Comment’ to the ‘State’ field and by abusing a deserialization call we can achieve remote code execution. Code to inject the payload to achieve RCE
Code for RCE
SOC analysis of the vulnerability
In order to do a forensic analysis I would like to use the Hack-The-Box platform's sherlock exercise:
The challenge had two files:
I-like-to-27a787c5.vmem {windows event trace log}
Triage.zip Triage.zip had a results folder containing results from
kapetool

The data they provided to detect was:
MFT (
Triage/uploads/ntfs/%5C%5C.%5CC%3A/$MFT)IIS logs (
Triage/uploads/auto/C%3A/inetpub/logs/LogFiles/W3SVC2/u_ex230712.log)PowerShell History Files (
Triage/uploads/auto/C%3A/users/)Event Logs (
Triage/uploads/auto/C%3A/Windows/System32/winevt/Logs/)SQLdump (
Triage/uploads/moveit.sql)Memory dump (
I-like-to-27a787c5.vmem)Registry hives (
Triage/uploads/auto/C%3A/Windows/System32/config/)
IIS logs
in the C:\inetpub directory -> In Triage/uploads/auto/C%3A/inetpub There was a Logfiles Folder which had: W3SVC2 folder containing the file: u_ex230712.log When searched for the moveit in the logs I got the human.aspx : the indication of the attack , as the same files were uploaded and searched for in the logs as per the above python exploit we saw

also the ip of the attackeR: 10.255.254.3. To confirm our hypothesis we get the requested resources from the files with the command:
The most requested resource is :The one we look ed above in the exploit that makes

Also what kind of client searches for nmap:

looks like there was a scan of nmap:

we need to look for these requests:
GET
/MOVEitISAPI/MOVEitISAPI.dll?action=2POST
/machine2.aspxPOST
/guestaccess.aspxPOST
/api/v1/tokenGET
/api/v1/foldersPOST
/api/v1/folders/{id}/files?uploadType=resumablePUT
/api/v1/folders/{id}/files?uploadType=resumable&fileId={id}and look what we have here:
The whole pattern is somehow getting mimicked:

console history
Looks like someone wanted something badly:

Memory Analysis
We also were provided with the memory dump of the file -> we extract the strings from the file:
we get this from the file:

This is how the webshell was downloaded
Passoword change via attacker
In the windows the password change is done via the net user command so when I grepped the string:

So this is the whole attack scenario we need to look for as an SOC.
Mitigation
Recommended Actions to Address MOVEit Transfer Vulnerability:
To prevent the exploitation of the identified vulnerability in MOVEit Transfer, it is crucial to apply immediate remediation measures. Progress has provided the following recommendations to mitigate the risk:
Update MOVEit Transfer: Ensure that you update your MOVEit Transfer installation to one of the following patched versions:
MOVEit Transfer 2023.0.1
MOVEit Transfer 2022.1.5.
MOVEit Transfer 2022.0.4
MOVEit Transfer 2021.1.4.
MOVEit Transfer 2021.0.6
YARA rule for the vulnerability: Github
Disable HTTP and HTTPS Traffic: Modify your firewall rules to block all incoming HTTP and HTTPS traffic to the affected MOVEit Transfer products. Specifically, deny traffic on ports 80 and 443. This step helps prevent potential attacks targeting the vulnerability.
Remove Unauthorized Files and User Accounts: Immediately delete any unauthorized files, particularly instances of “human2.aspx”, from your MOVEit Transfer environment. Additionally, carefully review the user accounts associated with the system and eliminate any suspicious or unauthorized accounts to minimize the risk of unauthorized access.
References
Last updated